Cybersecurity for SMBs is generally treated as a requirement that offers little value beyond meeting the requirement of having it. The problem with that attitude is that it may lead business owners to make hasty decisions about their cybersecurity strategy. Hasty decisions can cause you to overpay for poor results.
| “While everyone needs cybersecurity, not every cybersecurity plan will be the same. That’s why you must focus on what’s best for your business. Treat general best practices as your starting point.” – Ethan Gillani, CEO of Micro-Tech USA. |
The stronger your cybersecurity solutions, the better, but that doesn’t necessarily mean that you always need to pay for tools that you don’t need. Often, you can achieve powerful cybersecurity without relying on highly advanced technology. In many cases, there are simple solutions that SMBs can practically implement.
This guide will explore these options. We will also help you assess whether your current cybersecurity strategy is delivering the value that you expect.
Practical SMB Cybersecurity Solutions That Quickly Deliver Value
Multi-factor Authentication
Multi-factor authentication (MFA) adds an extra step to logging in (usually a code sent to your phone or an app confirmation). It protects your accounts even if someone guesses or steals a password.
You can turn on MFA in tools like Microsoft 365, cloud apps, and financial platforms. It only takes a few minutes to set up and provides immediate protection. Microsoft even claims that this simple step will block 99.2% of all cyber threats.
Automated Patch Management
Patch management ensures your software and devices are always up to date with the latest security fixes. These updates often close security gaps that attackers look for.
Using automated tools, your team or provider can apply updates behind the scenes with little disruption to daily work. This reduces the chance of a known vulnerability being used against your systems.
Patch Your IT Systems & Enjoy 99.9% IT Network Uptime.
Phishing Simulations
Phishing simulations help your employees learn how to identify fake emails before they reach them. These safe, test emails resemble real phishing messages and reveal who might click on them by mistake. After each test, employees who fall for the bait get a short training session. Over time, your staff becomes more adept at identifying suspicious messages, which reduces your risks quickly.
Remote Access Controls
Remote access enables employees to connect to your systems from outside the office, but it can also expose you to security threats if not properly managed.
Simple actions, such as turning off unused remote tools, requiring a second layer of login, and keeping access software up to date, can significantly reduce this risk. These changes enhance security without complicating the staff’s job responsibilities.
Backup Validation
A data backup is only useful if it works when you need it. Backup validation drills test whether you can recover files or systems during an emergency.
Schedule regular test runs of your backups, even if just once per quarter. This confirms you can restore key data and reduces the chance of long downtime after a failure or ransomware attack.
Endpoint Detection & Response
Endpoint detection and response (EDR) software monitors your computers, servers, and mobile devices in real-time for suspicious activity.
If it spots anything unusual, it can stop the activity before it spreads. EDR tools run quietly in the background and act quickly. They help reduce damage and recovery time if something gets past your defenses.
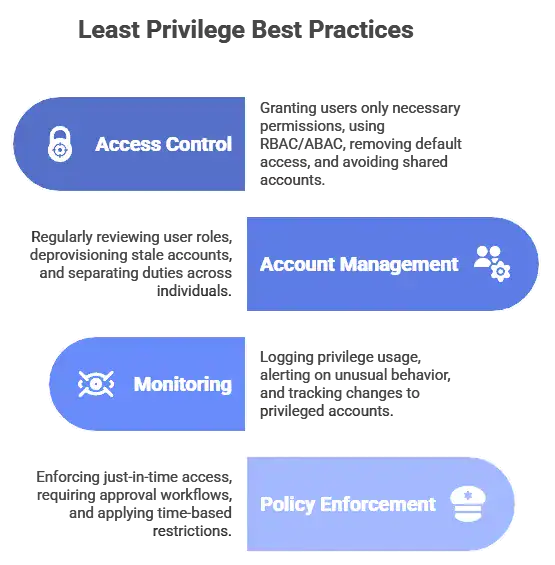
Least Privilege Policies
This approach gives each employee access to only the tools and information they need for their role. It limits how far an attacker could get if an account is ever compromised.
Review who has admin access and remove any unnecessary permissions. Making this change doesn’t affect daily work but reduces long-term risk.
Staff Security Training
Employee error causes 35% of data breaches. In the other 65% of cases involving external threat actors, internal errors created the opportunity in 95% of them. Needless to say, security awareness training may be your most valuable cybersecurity strategy.
Short, regular training sessions keep security top of mind. Many organizations see better results from brief sessions every few months than from long annual courses. It’s one of the fastest ways to strengthen your defenses.
How to Assess The ROI of Your Cybersecurity Program
1. Define Measurable Objectives
Begin by defining what your cybersecurity program aims to accomplish. This includes maintaining customer data security, minimizing downtime, meeting compliance requirements, and preventing financial loss.
Write these goals down in plain language. Avoid vague phrases like “improve security.” Instead, focus on specific outcomes such as “reduce phishing-related downtime” or “meet insurance policy conditions.”
2. Identify Key Metrics
Once your goals are clear, decide how to measure progress. Choose metrics that tie back to business impact. For example, fewer incidents or faster recovery times can directly reduce financial and operational risk.
Here are a few more key examples.
| Metric | Description | Business Impact |
| Mean Time to Detect (MTTD) | Average time to identify a threat or malicious activity | Reduces dwell time and limits potential damage |
| Mean Time to Respond (MTTR) | Average time to contain or mitigate a threat after detection | Minimizes the risk of data loss and reduce the amount of time malicious code has to spread |
| Incident Volume | Number of confirmed security incidents over a given period | Highlights threat trends and resource demand |
| Phishing Click Rate | Percentage of users who click simulated phishing emails | Tracks user awareness and training effectiveness |
| Privileged Access Violations | Instances where privileged accounts were misused or accessed improperly | Identifies risk tied to elevated permissions |
| Endpoint Detection Coverage | Percentage of devices protected by endpoint detection and response (EDR) tools | Indicates exposure level across the environment |
| Unpatched Critical Vulnerabilities | Number of known critical vulnerabilities not yet remediated | Signals risk tied to delayed patching |
| Failed Authentication Attempts | Volume of failed login attempts by user or system | May indicate brute-force or credential stuffing attempts |
| Data Exfiltration Alerts | Number of alerts tied to possible unauthorized data transfers | Tied directly to the risk of threat actors gaining access to systems |
| MFA Adoption Rate | Percentage of users with multi-factor authentication enabled | Low adoption increases account compromise risk |
3. Track Trends
Look at where you started and how things have changed since the program began. Plot this information over time. A consistent drop in phishing clicks or faster patch turnaround shows the program is working. If the numbers stay flat or get worse, dig into why.
4. Estimate Cost Avoidance
Review past security events, or common threats you’ve blocked, and estimate how much they could have cost in downtime, lost business, or recovery expenses.
Use conservative estimates based on your business’s size and actual impact. For example, if you’ve prevented three ransomware attempts and each could have caused three days of downtime, you can calculate what you likely saved in lost productivity and remediation costs.
5. Compare With Program Costs
Gather the full cost of your cybersecurity program. Include staff time, tools, training, services, and IT consultants. Then, weigh those costs against the value you’ve protected. This helps show whether your investment is proportionate to the risk it reduces.
6. Reassess Regularly
ROI isn’t fixed. It changes as your business grows or as threats evolve. Set a regular check-in, such as once a year, to revisit your goals, review your metrics, and adjust your priorities.
Use these reviews to identify gaps or reinforce what’s working. This keeps your cybersecurity spending aligned with your current business needs.
How to Enhance ROI If There Are Gaps In Your Program
1. Refocus on Business Risks
Start by reconnecting your cybersecurity goals with actual business risks. Instead of reacting to general threats, review what matters most to your operations. Realigning your program this way avoids wasted effort on issues that don’t affect your bottom line and helps target improvements where they’ll deliver better value.
2. Tighten Program Scope
If the program feels too broad or unfocused, narrow it. Prioritize fixes and tools that protect high-impact systems or help your team respond faster. You don’t need to cover everything at once. A smaller, well-executed focus area often delivers better returns than spreading effort across too many fronts.
| Get More Insights on How You Can Optimize Your IT Systems |
3. Improve Process Consistency
Even the best tools underperform if staff skip steps or follow different procedures.
Review how consistently tasks like patching, access reviews, and user training are completed. Standardize key processes and assign ownership to specific roles. This helps close gaps and brings more predictability to your outcomes.
4. Encourage User Involvement
Employees play a major role in cybersecurity, but programs often treat them as passive recipients of policies.
Instead, involve them in feedback, short awareness surveys, or real-world practice sessions. This raises accountability, builds internal support, and makes future investments in training or behavior change more effective.
5. Reassess Vendors
If your security provider or tools haven’t kept up with your needs, it may be time to revisit those partnerships. A vendor that can’t show results or explain its value isn’t helping your ROI. Ask for performance reviews, reports, or clear next steps. Hold partners to the same ROI expectations you set for your own team.
| Find a New Cybersecurity Partner in The Midwest | |
| Chicago, IL | Milwaukee, WI |
Work With Experts In Cybersecurity For SMBs
If you’re feeling stuck with an ineffective cybersecurity program, you don’t have to be. All you need to do is find someone who can show you how to secure sensitive data and do most of the heavy lifting on your behalf.
Micro-Tech USA can do that work. We can help you reduce attack vectors, establish incident response plans, and so much more. All that you need to do is tell us about your IT systems, cybersecurity needs, and business goals.
Contact us today to get started.







